Fortify Your Freight: Essential Tips for Cargo Security

From the moment goods are loaded onto a vessel to their safe arrival at the destination port, numerous threats can jeopardize their safety. This comprehensive guide delves into the essential strategies and best practices for cargo security, offering ship owners invaluable insights to protect their shipments from theft, damage, and other risks. Join us as we explore the critical aspects of safeguarding your cargo, drawing on real-world examples and expert recommendations to help you navigate the challenges of modern shipping.
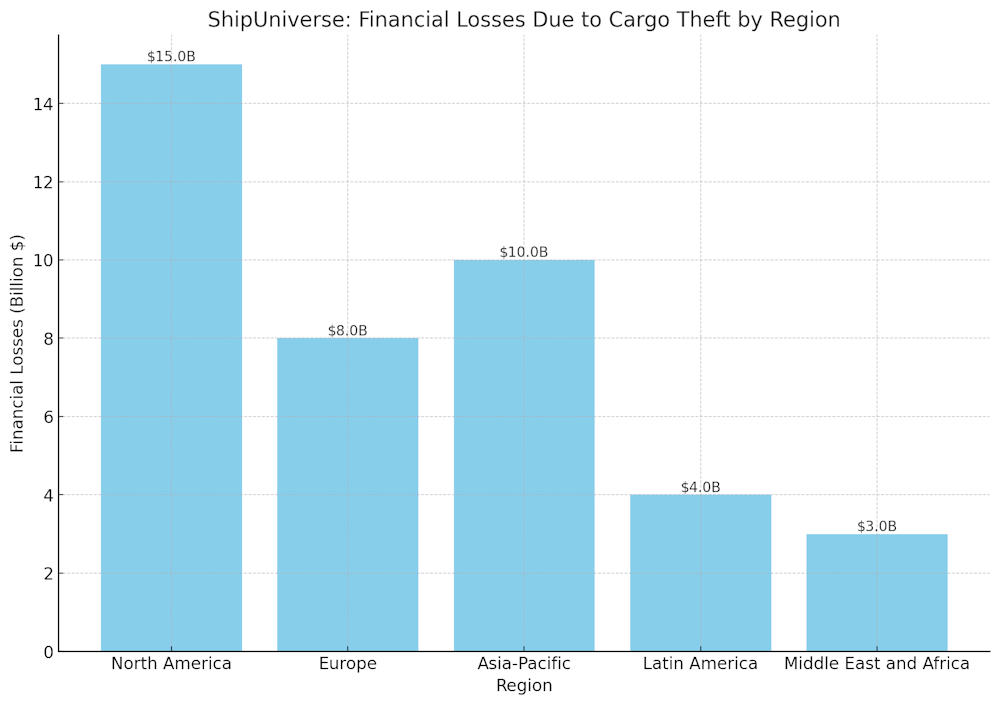
Importance of Cargo Security in the Shipping Industry
- Economic Impact: Cargo theft and damage result in significant financial losses for shipping companies, insurers, and customers.
- Reputation: Poor cargo security can damage a company’s reputation, leading to loss of business and customer trust.
- Regulatory Compliance: Ensuring cargo security is essential for compliance with international regulations and standards.
- Safety: Proper cargo security measures protect the safety of crew members and the integrity of the shipping vessel.
Potential Risks and Consequences of Poor Cargo Security
- Financial Losses: Direct losses from theft and damage, increased insurance premiums, and potential legal costs.
- Operational Disruptions: Delays in delivery schedules, increased turnaround times, and disrupted supply chains.
- Legal and Regulatory Penalties: Fines and sanctions from non-compliance with security regulations.
- Reputational Damage: Loss of customer trust and potential loss of future business.
- Safety Hazards: Increased risk of accidents and injuries to crew members.
Understanding Cargo Security
- Cargo Security: Measures and protocols implemented to protect cargo from theft, damage, and unauthorized access during transit and storage.
- Scope:
- Physical Security: Protecting the physical integrity of the cargo through proper packaging, sealing, and stowage.
- Access Control: Restricting access to cargo areas and ensuring only authorized personnel handle the cargo.
- Surveillance and Monitoring: Utilizing technology to monitor and track cargo throughout the supply chain.
- Documentation and Procedures: Maintaining accurate records and following standardized procedures to ensure accountability and traceability.
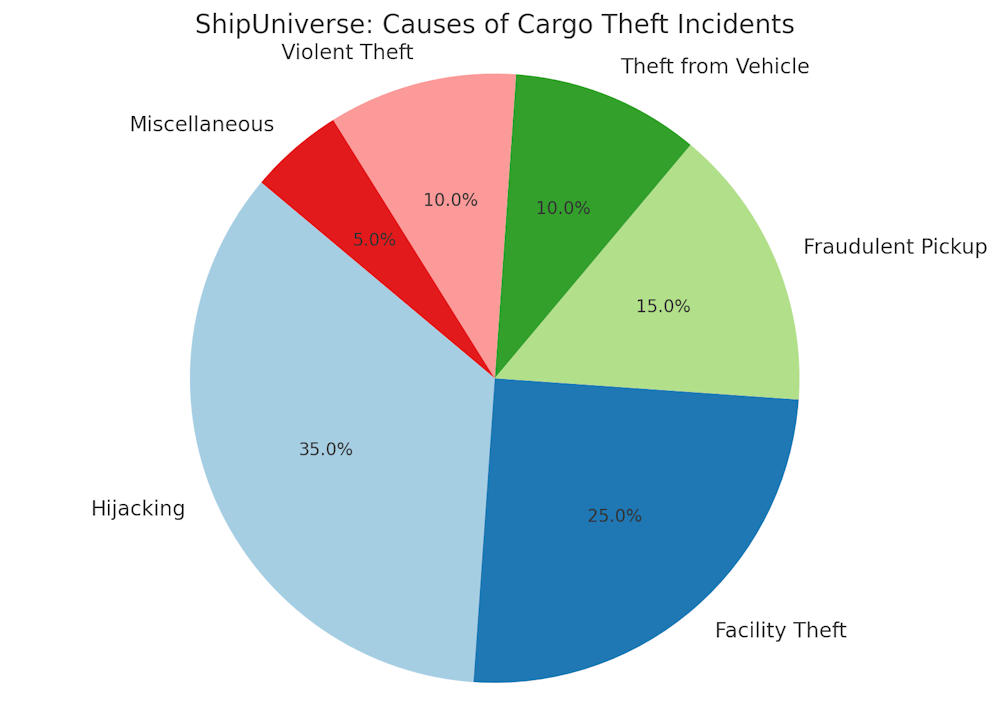
Key Threats to Cargo Security
- Theft: Unauthorized removal of cargo by external parties or insiders.
- Opportunistic Theft: Random thefts due to visible and easily accessible cargo.
- Organized Crime: Coordinated efforts by criminal groups to steal high-value cargo.
- Damage: Physical harm to cargo due to improper handling, stowage, or accidents.
- Handling Damage: Mishandling during loading, unloading, or transit.
- Environmental Damage: Exposure to adverse weather conditions or hazardous substances.
- Piracy: Attacks by pirates targeting cargo ships, especially in high-risk areas like the Gulf of Aden.
- Hijacking: Pirates taking control of the ship to demand ransom.
- Theft and Vandalism: Pirates stealing cargo or causing damage to the vessel.
- Unauthorized Access: Access by individuals without proper authorization, leading to theft, tampering, or sabotage.
- Internal Threats: Disgruntled employees or insiders with access to sensitive areas.
- External Threats: Stowaways or unauthorized personnel gaining access to cargo holds.
By understanding these foundational aspects of cargo security, stakeholders in the shipping industry can better prepare and implement effective security measures to safeguard their cargo and operations.
Risk Assessment and Management
Conducting a Thorough Risk Assessment
- Identify Risks: List potential risks to cargo security, including theft, damage, piracy, and unauthorized access.
- Evaluate Likelihood and Impact: Assess the likelihood of each risk occurring and its potential impact on operations and finances.
- Prioritize Risks: Rank risks based on their likelihood and impact to focus on the most critical threats first.
- Document Findings: Create a detailed report of the risk assessment, including identified risks, their evaluations, and prioritization.
Identifying Vulnerable Points in the Supply Chain
- Loading and Unloading Areas: Points where cargo is most vulnerable to theft and damage due to frequent handling and access by multiple parties.
- Transit Routes: High-risk areas during transit, such as regions known for piracy or areas with poor infrastructure and security.
- Storage Facilities: Warehouses and storage yards where cargo may be stored for extended periods, increasing the risk of theft or damage.
- Access Control Points: Areas where unauthorized personnel could gain access to cargo, such as port entrances, ship decks, and cargo holds.
- Documentation Processes: Vulnerabilities in paperwork and documentation that could lead to errors, fraud, or loss of cargo traceability.
Implementing Risk Management Strategies
- Security Protocols: Establish and enforce strict security protocols for loading, unloading, and handling cargo.
- Access Control: Implement measures like ID checks, security guards, and surveillance cameras to restrict access to cargo areas.
- Seals and Locks: Use tamper-evident seals and secure locks on containers and cargo holds.
- Technology Solutions: Leverage technology to enhance cargo security.
- GPS Tracking: Equip cargo with GPS tracking devices to monitor its location in real-time.
- RFID Tags: Use RFID tags to track individual items or containers, ensuring accurate inventory and preventing theft.
- Training and Awareness: Train staff and crew on security protocols and raise awareness about the importance of cargo security.
- Regular Drills: Conduct regular security drills to ensure that staff are prepared to handle security threats.
- Security Briefings: Provide periodic security briefings to update staff on new threats and security measures.
- Collaborative Efforts: Work with stakeholders across the supply chain to enhance security.
- Port Authorities: Collaborate with port authorities to ensure secure handling and storage of cargo.
- Insurance Providers: Work with insurance providers to understand coverage and requirements for cargo security.
- Continuous Improvement: Regularly review and update security measures to adapt to evolving threats.
- Security Audits: Conduct periodic security audits to identify and address vulnerabilities.
- Feedback Mechanisms: Establish mechanisms for staff to report security concerns and suggest improvements.
By conducting thorough risk assessments, identifying vulnerable points, and implementing effective risk management strategies, cargo ship owners can significantly enhance the security of their cargo and minimize potential losses.
Best Practices for Cargo Security
Securing Cargo During Transit
- Proper Stowage and Securing Methods
- Load Distribution: Ensure even distribution of cargo weight to maintain the ship’s balance and stability.
- Securing Devices: Use appropriate securing devices like lashing belts, nets, and ropes to prevent cargo from shifting during transit.
- Container Seals: Employ tamper-evident container seals to detect unauthorized access.
- Use of Seals and Locks
- High-Security Seals: Utilize high-security seals that are difficult to tamper with or replicate.
- Locks: Implement robust locking mechanisms for cargo holds and containers to deter theft and unauthorized access.
Security Measures at Ports and Terminals
- Access Control and Surveillance
- Restricted Access Zones: Designate restricted access zones within ports and terminals to limit entry to authorized personnel only.
- Surveillance Systems: Install CCTV cameras and other surveillance systems to monitor cargo areas continuously.
- Security Personnel: Deploy trained security personnel to patrol and monitor critical areas within the port.
- Collaboration with Port Authorities
- Security Protocols: Work with port authorities to establish and enforce consistent security protocols.
- Information Sharing: Share information on security threats and incidents with port authorities and other stakeholders to enhance overall security.
Technology in Cargo Security
- GPS Tracking and Monitoring Systems
- Real-Time Tracking: Equip cargo with GPS tracking devices to monitor its location and movement in real-time.
- Geofencing: Set up geofencing alerts to notify when cargo enters or exits predefined areas, enhancing security and logistics management.
- RFID Tags and Sensors
- RFID Technology: Use RFID tags to track individual items or containers, providing detailed inventory management and reducing the risk of theft.
- Environmental Sensors: Implement sensors to monitor environmental conditions such as temperature and humidity, ensuring sensitive cargo remains in optimal conditions.
Documentation and Procedures
- Accurate Record-Keeping
- Inventory Logs: Maintain detailed logs of all cargo items, including descriptions, quantities, and serial numbers.
- Chain of Custody: Document the chain of custody for cargo, tracking its movement from origin to destination to ensure accountability.
- Standardized Procedures
- Loading and Unloading: Establish standardized procedures for loading and unloading cargo to minimize the risk of damage and theft.
- Incident Reporting: Implement a system for reporting and documenting security incidents, ensuring timely response and corrective actions.
Regular Security Audits
- Periodic Reviews
- Audit Schedule: Conduct regular security audits to assess the effectiveness of existing security measures and identify areas for improvement.
- Audit Team: Assemble a team of security experts to perform comprehensive audits, including physical inspections and reviews of security protocols.
- Implementing Improvements
- Action Plans: Develop action plans based on audit findings to address identified vulnerabilities and enhance security measures.
- Follow-Up Audits: Schedule follow-up audits to ensure that corrective actions have been implemented effectively and to assess their impact.
By adhering to these best practices, cargo ship owners can create a robust security framework that protects their cargo from theft, damage, and other risks, ensuring smooth and secure operations.
Regulatory Compliance
Overview of International Regulations and Standards
- International Maritime Organization (IMO)
- SOLAS (Safety of Life at Sea): Mandates safety measures for cargo ships, including the safe stowage and securing of cargo.
- ISPS Code (International Ship and Port Facility Security): Provides a framework for ensuring the security of ships and port facilities against threats.
- Customs and Border Protection (CBP)
- C-TPAT (Customs-Trade Partnership Against Terrorism): A voluntary program that encourages businesses to ensure the integrity of their security practices and communicate their security guidelines to their partners.
- Maritime Labour Convention (MLC)
- Seafarers’ Rights: Ensures decent working conditions for seafarers, including safety measures related to cargo handling.
Compliance with ISPS (International Ship and Port Facility Security) Code
- Ship Security Assessment (SSA)
- Identifying Threats: Assess potential security threats and vulnerabilities specific to the ship and its operations.
- Security Measures: Implement measures to mitigate identified threats, including physical barriers, surveillance systems, and access controls.
- Ship Security Plan (SSP)
- Developing the Plan: Create a comprehensive security plan outlining procedures for different security levels and emergency situations.
- Implementation: Ensure that all crew members are trained and familiar with the security plan and their specific roles.
- Port Facility Security Assessment (PFSA)
- Risk Evaluation: Evaluate the security risks at port facilities and identify measures to address these risks.
- Collaboration: Work with port authorities to develop and implement a coordinated security strategy.
Documentation and Record-Keeping Requirements
- Security Records
- Logs and Registers: Maintain detailed logs of security incidents, training sessions, and security audits.
- Access Records: Keep records of all individuals who have access to cargo and secure areas, including contractors and visitors.
- Cargo Documentation
- Bill of Lading: Ensure that all cargo is accompanied by a properly completed bill of lading, detailing the contents, destination, and consignee.
- Customs Declarations: Accurately complete and submit all required customs declarations to avoid delays and fines.
- Audit Trails
- Regular Reviews: Conduct regular reviews of security records and documentation to ensure compliance and identify areas for improvement.
- Accountability: Assign responsibility for maintaining and reviewing security records to specific individuals or teams.
Training and Certification
- Crew Training
- Security Awareness: Provide regular training sessions on security awareness, including recognizing and responding to security threats.
- Emergency Procedures: Train crew members on emergency procedures, including how to handle security breaches and other incidents.
- Certification Programs
- ISPS Code Certification: Obtain certification under the ISPS Code to demonstrate compliance with international security standards.
- Other Certifications: Consider additional certifications relevant to cargo security, such as C-TPAT for international trade.
By ensuring regulatory compliance, cargo ship owners can not only avoid legal and financial penalties but also enhance the overall security and efficiency of their operations.
Training and Awareness
Training Programs for Crew and Staff
- Security Awareness Training
- Threat Recognition: Teach crew and staff how to recognize potential security threats, such as suspicious behavior or unauthorized access attempts.
- Reporting Procedures: Train personnel on the proper procedures for reporting security incidents and suspicious activities.
- Regular Updates: Provide ongoing training to keep crew and staff updated on new security threats and best practices.
- Emergency Response Training
- Incident Response: Train crew members on how to respond to various security incidents, including theft, piracy, and unauthorized access.
- Evacuation Drills: Conduct regular evacuation drills to ensure all personnel know how to safely evacuate the vessel in case of an emergency.
- Crisis Management: Develop and practice crisis management procedures to handle emergencies effectively.
Building a Culture of Security Awareness
- Leadership Commitment
- Top-Down Approach: Ensure that senior management is committed to cargo security and sets an example for the rest of the organization.
- Security Policies: Develop and enforce clear security policies that emphasize the importance of cargo security.
- Employee Engagement
- Security Briefings: Hold regular security briefings to keep all employees informed about current security issues and measures.
- Feedback Mechanisms: Establish channels for employees to report security concerns and provide feedback on security measures.
- Incentives and Recognition
- Reward Programs: Implement reward programs to recognize employees who demonstrate exceptional vigilance and commitment to security.
- Positive Reinforcement: Use positive reinforcement to encourage adherence to security protocols and procedures.
Regular Drills and Security Audits
- Conducting Regular Drills
- Scenario-Based Drills: Perform scenario-based drills to simulate different security incidents and test the crew’s response.
- Frequency: Schedule drills at regular intervals to ensure preparedness and identify areas for improvement.
- Debriefing Sessions: Hold debriefing sessions after each drill to discuss performance, identify weaknesses, and develop corrective actions.
- Performing Security Audits
- Internal Audits: Conduct regular internal audits to assess the effectiveness of existing security measures and protocols.
- External Audits: Engage third-party security experts to perform external audits and provide an unbiased evaluation of security practices.
- Audit Reports: Document audit findings in detailed reports and use these to make informed decisions on improving security measures.
Developing an Incident Response Plan
- Comprehensive Plan
- Roles and Responsibilities: Define clear roles and responsibilities for all personnel involved in the incident response.
- Response Procedures: Outline specific procedures for responding to different types of security incidents, such as theft, piracy, and unauthorized access.
- Communication Protocols: Establish communication protocols to ensure timely and effective communication during an incident.
- Training and Simulation
- Plan Training: Train all relevant personnel on the incident response plan to ensure they understand their roles and responsibilities.
- Simulation Exercises: Conduct simulation exercises to test the effectiveness of the incident response plan and identify areas for improvement.
By investing in comprehensive training programs and fostering a culture of security awareness, cargo ship owners can significantly enhance the security of their operations and ensure that their crew and staff are well-prepared to handle any security threats that may arise.
Incident Response and Recovery
Developing an Incident Response Plan
- Roles and Responsibilities
- Designated Response Team: Establish a designated response team with clear roles and responsibilities for handling security incidents.
- Chain of Command: Define a clear chain of command to ensure efficient decision-making and coordination during an incident.
- Crew Involvement: Ensure all crew members understand their specific roles in the response plan.
- Response Procedures
- Initial Assessment: Develop procedures for the initial assessment of the incident to determine its scope and impact.
- Immediate Actions: Outline immediate actions to be taken to mitigate the impact of the incident, such as securing the affected area and informing relevant authorities.
- Communication Protocols: Establish communication protocols for internal and external communication during an incident.
Steps to Take in Case of a Security Breach
- Containment and Control
- Isolate the Incident: Quickly isolate the affected area to prevent further damage or unauthorized access.
- Secure Evidence: Secure and preserve evidence related to the incident for further investigation.
- Coordinate with Authorities: Notify and coordinate with relevant authorities, such as port security or law enforcement agencies.
- Assessment and Reporting
- Incident Reporting: Report the incident according to established protocols, including detailed documentation of the event.
- Impact Assessment: Conduct a thorough assessment of the impact on operations, cargo, and personnel.
- Root Cause Analysis: Perform a root cause analysis to identify the underlying factors that led to the security breach.
- Recovery Actions
- Mitigation Measures: Implement measures to mitigate the impact of the incident, such as rerouting cargo, adjusting schedules, and repairing damages.
- Crew Support: Provide support to crew members affected by the incident, including medical care and counseling if necessary.
- Communication with Stakeholders: Communicate with stakeholders, including customers and partners, to inform them of the incident and steps being taken to address it.
Post-Incident Analysis and Recovery
- Post-Incident Review
- Debriefing Sessions: Conduct debriefing sessions with the response team and crew to review the incident and response actions.
- Identify Lessons Learned: Identify lessons learned from the incident and response to improve future preparedness.
- Update Response Plan: Update the incident response plan based on the insights gained from the post-incident review.
- Implementing Improvements
- Security Enhancements: Implement enhancements to security measures and protocols to prevent similar incidents in the future.
- Training Updates: Update training programs to incorporate lessons learned and improve crew preparedness.
- Continuous Monitoring: Establish continuous monitoring to ensure the effectiveness of implemented improvements and identify emerging threats.
- Documentation and Reporting
- Detailed Reports: Prepare detailed reports on the incident, response actions, and recovery efforts for internal records and regulatory compliance.
- Stakeholder Communication: Communicate the outcomes of the post-incident analysis and improvements to stakeholders to maintain transparency and trust.
By developing a comprehensive incident response plan and ensuring thorough post-incident analysis and recovery efforts, cargo ship owners can effectively manage and mitigate the impact of security breaches, enhancing the overall security and resilience of their operations.
Recap of Key Points
- Importance of Cargo Security: Cargo security is vital for protecting financial assets, maintaining operational efficiency, ensuring regulatory compliance, and safeguarding crew members’ well-being.
- Comprehensive Approach: Effective cargo security requires a multi-faceted approach, including risk assessment, implementing best practices, regulatory compliance, crew training, and a robust incident response plan.
- Real-World Examples: Learning from real-world incidents and success stories can provide valuable insights and strategies for enhancing cargo security measures.
Continuous Improvement in Cargo Security
- Ongoing Risk Assessment: Regularly conduct risk assessments to identify and address new vulnerabilities.
- Adapting to New Threats: Stay informed about emerging threats and continuously update security measures to counteract them.
- Investing in Technology: Leverage the latest technology to improve tracking, monitoring, and overall security of cargo.
- Training and Awareness: Ensure continuous training and awareness programs for crew and staff to keep them prepared for any security challenges.
Final Thoughts and Recommendations
- Collaborative Efforts: Collaborate with all stakeholders, including port authorities, insurers, and regulatory bodies, to create a comprehensive and coordinated security strategy.
- Proactive Measures: Adopt a proactive approach to cargo security, anticipating potential threats and implementing measures to mitigate them before they occur.
- Regular Audits and Reviews: Perform regular security audits and reviews to ensure that all security protocols are up to date and effective.
- Customer Communication: Maintain open communication with customers about security measures and protocols to build trust and transparency.
By taking a proactive and comprehensive approach to cargo security, ship owners can significantly reduce the risks associated with cargo theft, damage, and other security threats. Ensuring the safety and security of cargo not only protects financial interests but also enhances the reputation and operational efficiency of the shipping company.
Additional References
International Maritime Organization (IMO)
- Description: The IMO is a specialized agency of the United Nations responsible for regulating shipping. The organization focuses on areas such as safety, environmental concerns, legal matters, technical cooperation, maritime security, and the efficiency of shipping.
- URL: International Maritime Organization (IMO)
Transported Asset Protection Association (TAPA)
- Description: TAPA is a professional association of high-value asset protection specialists from various sectors such as manufacturers, logistics providers, freight carriers, law enforcement agencies, and others. It focuses on minimizing cargo theft risks.
- URL: Transported Asset Protection Association (TAPA)
World Shipping Council (WSC)
- Description: The World Shipping Council is an association of liner shipping companies that provides a coordinated voice for the industry in matters of international trade policy, security, environmental protection, and regulatory affairs.
- URL: World Shipping Council (WSC)
U.S. Customs and Border Protection (CBP)
- Description: CBP is the largest federal law enforcement agency of the United States Department of Homeland Security. It is charged with regulating and facilitating international trade, collecting import duties, and enforcing U.S. regulations, including trade, customs, and immigration.
- URL: U.S. Customs and Border Protection (CBP)
International Chamber of Commerce (ICC)
- Description: The ICC is the world’s largest business organization, working to promote international trade and investment, responsible business conduct, and a global approach to regulation. The ICC works to drive inclusive growth and prosperity through its network of over 45 million businesses in more than 100 countries.
- URL: International Chamber of Commerce (ICC)
European Maritime Safety Agency (EMSA)
- Description: EMSA provides technical assistance and support to the European Commission and EU Member States in the development and implementation of EU maritime safety legislation. It aims to ensure a high, uniform, and effective level of maritime safety and environmental protection.
- URL: European Maritime Safety Agency (EMSA)
International Organization for Standardization (ISO)
- Description: ISO is an independent, non-governmental international organization that develops and publishes international standards. The organization ensures that products and services are safe, reliable, and of good quality, providing guidance for various industries, including shipping.
- URL: International Organization for Standardization (ISO)
Maritime and Port Authority of Singapore (MPA)
- Description: MPA is a statutory board under the Ministry of Transport of the Government of Singapore. It oversees the development and growth of the maritime sector in Singapore, ensuring the safety and security of maritime navigation.
- URL: Maritime and Port Authority of Singapore (MPA)

Do you have a Maritime Product or Service that may be of interest to Shipowners? Tell us about it here!
Do you have feedback or insights? Please reach out to editor @ shipuniverse.com



